WiCYS CyberStart (Tokyo) Challenge 1
Hex text

Hello fellow Cyberstart gamers!
Having touched base 2 on our CyberStart journey, in Tokyo, it's time again to solve some security challenges. We are handed an appreciation letter and an overview of the challenges on the horizon
Briefing L02 C01
610enC0de’d Password
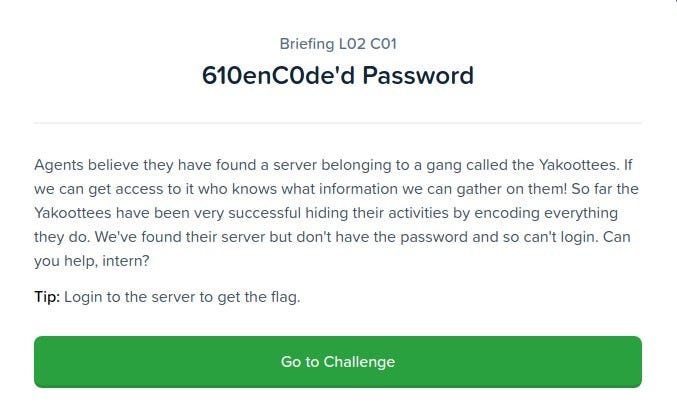
Agents believe they have found a server belonging to a gang called the Yakoottees. If we can get access to it who knows what information we can gather on them! So far the Yakoottees have been very successful hiding their activities by encoding everything they do. We’ve found their server but don’t have the password and so can’t login. Can you help, intern?
Tip: Login to the server to get the flag.
Proceeding to the challenge, we are met with this terminal screen
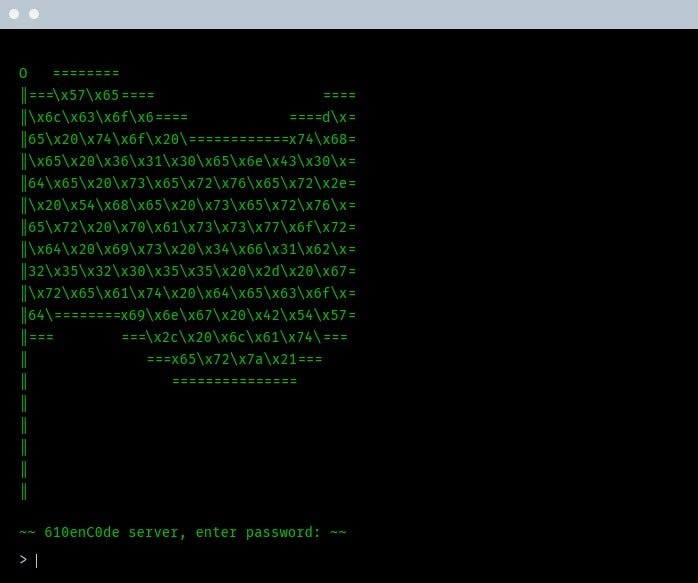
At first glance, this text looks like it has been encoded in hex form. Our job is to now decode it, to gain access to Yakoottees’ server.
Flag Capture
For that, I would suggest you use this resource. Others were not able to decode the hex-encoded text and you will see why. Copy-paste the hex code and decode it
This is our output
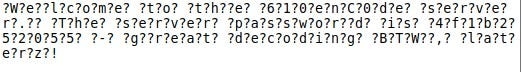
The cleartext looks a bit messy, doesn't it? Let’s clean it up
From our research, it is found that ‘?’ is represented as \x63 in hex code
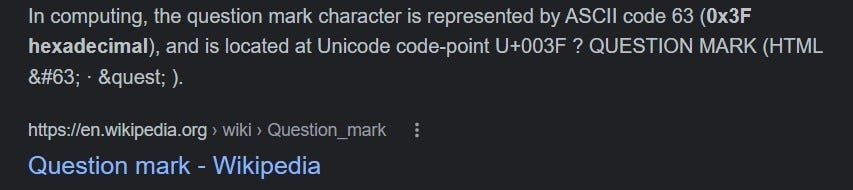
I was able to find just 2 instances of \x63, but it did not make the output any cleaner
From the jumbled decoded text, we can decipher the password (by removing question marks)
Password = 4f1b252055
Using it to login onto the server
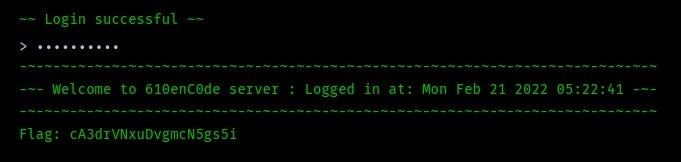
Flag — cA3drVNxuDvgmcN5gs5i
We are in, and the challenge is conquered!
Scoreboard

Onward Ahoy!
Last updated