WiCYS CyberStart (Tokyo) Challenge 2
Javascript Vulnerability

Briefing L02 C02
Spinlock
A large bank has refitted all of their vaults with the new SpinLock Extreme. As fancy as it sounds we believe it has a rather critical vulnerability, one we think the Yakoottees have been exploiting in a series of recent bank robberies.
The physical vault itself requires a special keycard to be inserted which, after checking the authenticity of the card, re-aligns the circular locking mechanism to unlock it and updates the interface to show it’s unlocked. However, we believe that the organisation has been remote accessing the interface on the vault, and unlocking the vault by doing it in reverse: getting the interface to unlock, which unlocks the physical vault itself. If we can confirm the method, we’ll be one step closer to understanding how this cyber gang operates!
Tip: Unlock the vault to get the flag.
Proceeding to challenge 2, we are met with this awesome-looking spinlock

What we can see is the circulating halo around the horizontal bar. Our objective is to make the red circle reach the middle of the halo.
I was pretty confused and stumped on how to proceed.
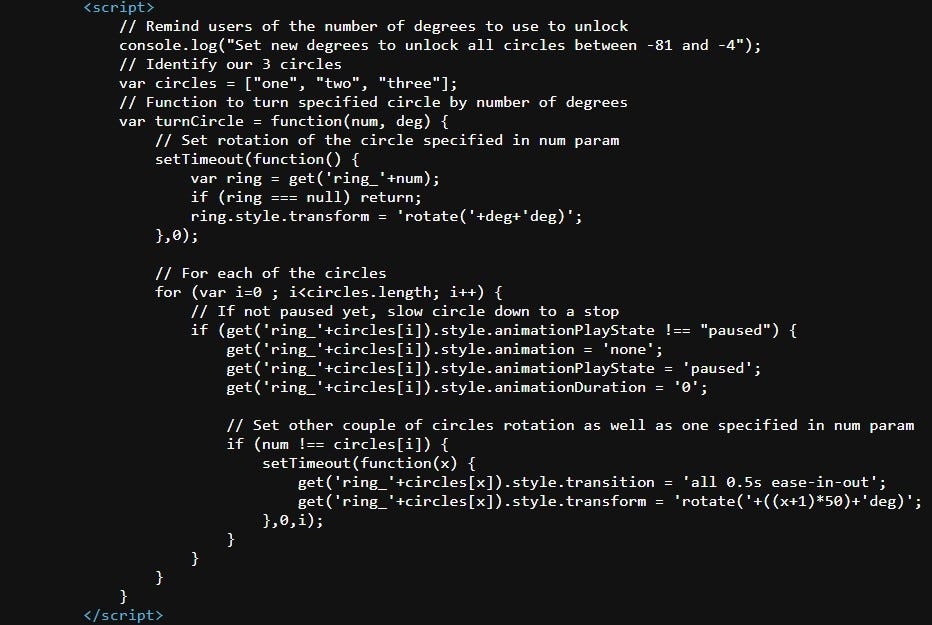
Having a look at the source code, we can see some Javascript code here
Admittedly, I was not able to progress from this challenge on my own, so took help from this online forum
The solution to crack the lock
What you need to do is to Right Click ->‘Inspect Element’ and then go to the Console
Type in these commands
What are we doing here?
This challenge contains a few bad practices which make the “Spinlock Extreme” bank vault not a secure solution and so vulnerable.
It contains unobfuscated and even well commented JavaScript, easily found in the source of the webpage. A hacker can easily find, read and use this function, which is likely what the Yakoottees found and so made use of. Even worse, being a client side only security solution for authorisation tends to be a bad practice, as code can be tampered with (as is happening here), to bypass security logic; server side authotisation should be made of and it isn’t here.
So to sum up the vulnerabilites — unobfuscated, easily found and understandable JavaScript, used for security logic with no server side component.
Trying to invoke the turnCircle function, we are trying to unlock the spinlock, aided with the degree measurement

Flag Capture
Doing so will unlock the spinlock and we will get our flag

Flag — GQAfbpYwacpgqPrI9KXa
Scoreboard

Onward ahoy to the next challenge!

Last updated