ShellShock Attack: Let’s Defend Challenge
Shellshock attack evidence analysis

Gist of the challenge
What is the Shellshock Vulnerability?
Challenge Questions
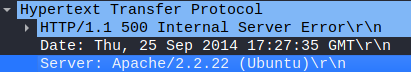
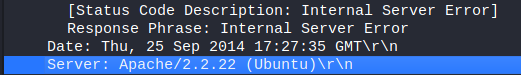
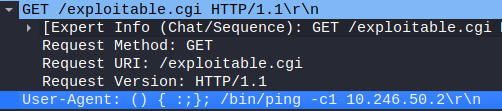
Conclusion
Your opinion matters
Last updated