SOC137 — Malicious File/Script Download Attempt: A Walkthrough
Powershell-fuelled malware
Welcome blue teamers!
Now, who is ready to do some SOC alert practice? Today I will be guiding you through the SOC 137 (Malicious File/Script Download Attempt) alert.
NOTE: Always remember to investigate alerts from Let’s Defend, on a VM.
Introduction to the Alert
Preceding the investigation, we are given a rundown of the alert summary. It contains vital information that comes in handy later
Take ownership
Create case
Start Playbook

Now, let’s delve into the questions
Define Threat Indicator
Select Threat Indicator

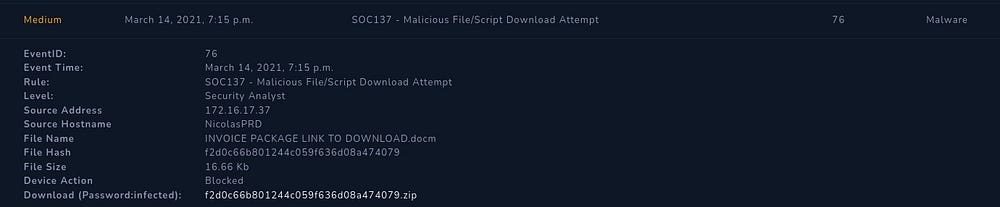
From the alert summary, we can find that the malicious .zip file was downloaded onto the NicolasPRD endpoint, with IP Address — 172.16.17.37
Upon unzipping it, we uncover a file named ‘INVOICE PACKAGE LINK TO DOWNLOAD.docm’
Enumeration and Analysis
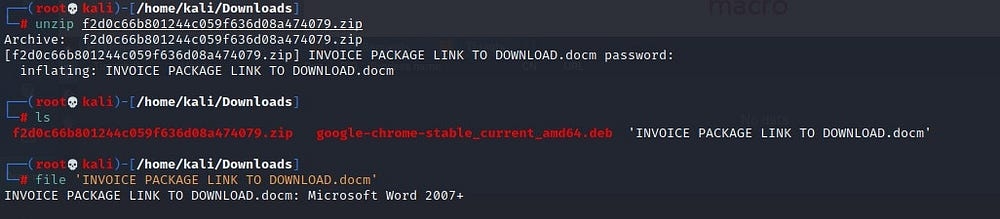
Applying Linux’s file command, we determine that the version of Microsoft Word used is from 2007
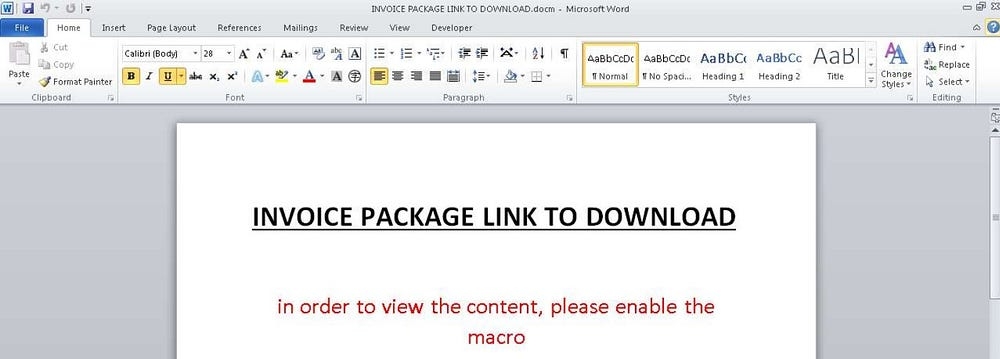
It would be wise to give the malicious file a run on Anyrun. It is much safer that way. Upon uploading, we find its contents below
Process breakdown
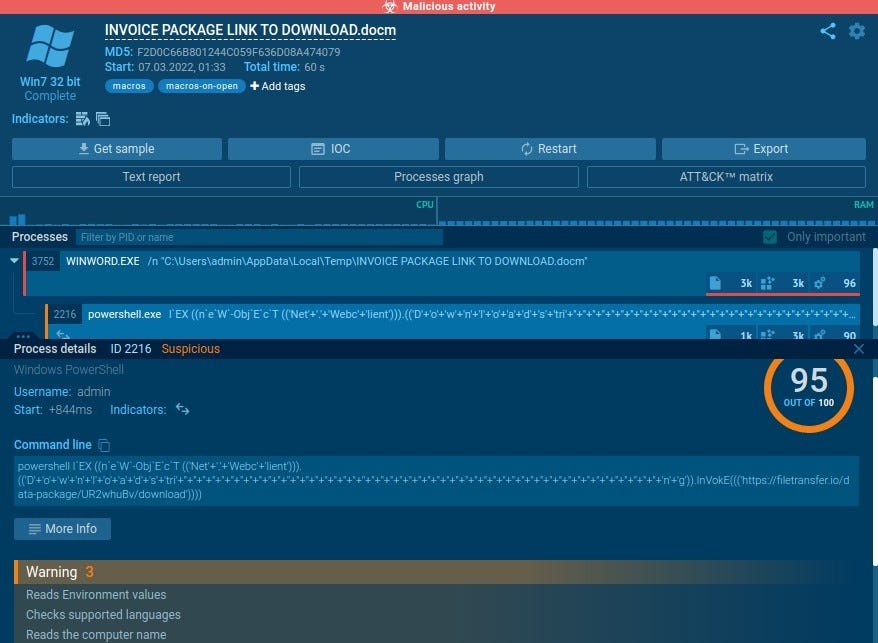
From the process tree of the malicious file, we can see that it has a PowerShell executable as a subprocess. The executable is given read permissions, which can be fatal, if not monitored properly.
This becomes evident especially when it has a 95% severity rate of being suspicious
Analysis using VirusTotal
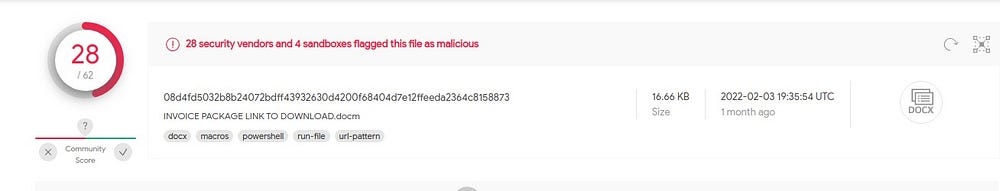
Analysis using VirusTotal
Making use of Hybrid-Analysis, we have received conclusive evidence of the file being malicious. Malicious and Suspicious IOCs have been identified and displayed below
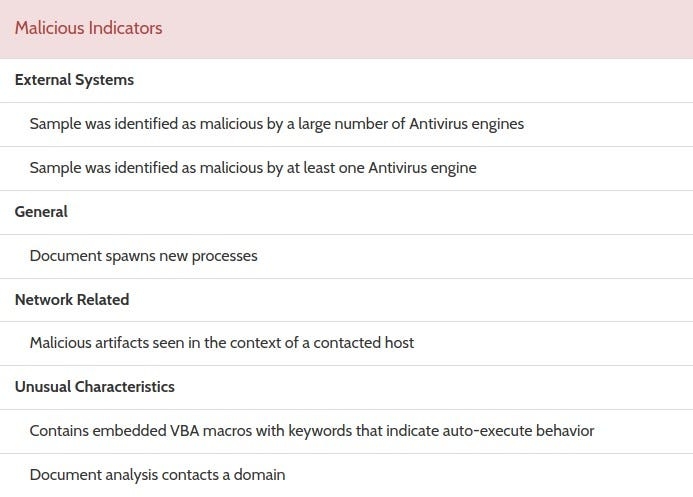

Judging from the evidence and characteristics of the malicious file collected above, we can conclude that the file contacts external domains, through undetected outgoing network traffic
A)Unknown or unexpected outgoing internet traffic
Check if the malware is quarantined/cleaned

I believe that the malware hasn't been quarantined
A)Not Quarrantined
Analyze Malware
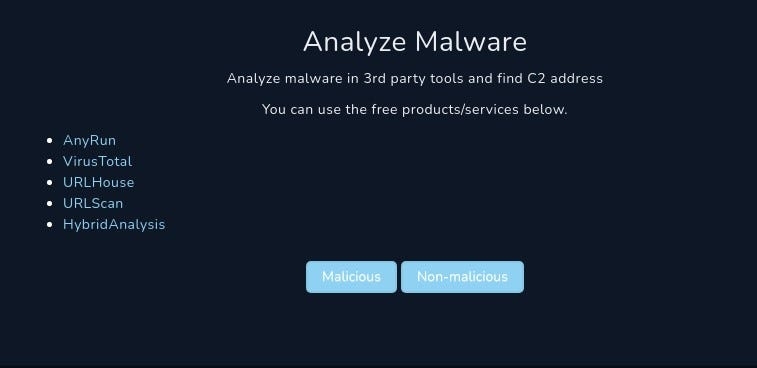
Analyze malware in 3rd party tools and find C2 address
You can use the free products/services below.
AnyRun VirusTotal URLHouse URLScan HybridAnalysis
From our analysis, we have concluded that the file is indeed malicious
A)Malicious
Check If Someone Requested the C2
Please go to the “Log Management” page and check if the C2 address accessed. You can check if the malicious file is run by searching the C2 addresses of the malicious file.
Log Management Please click “Yes” if someone access the malicious address. Otherwise please click “No” button.
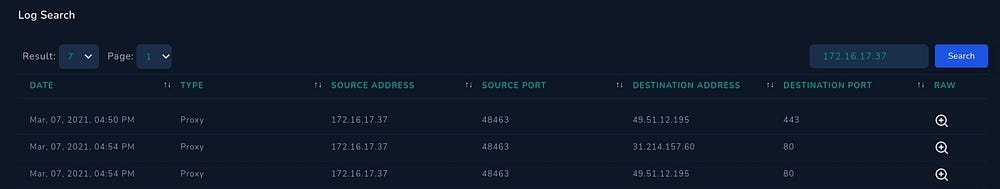
Let’s look up the source IP Address (172.16.17.37) on the Log Management section
We get 3 corresponding log entries, but none of them relate to the alert or show any reference to the download of a malicious file (as briefed to us)
Using Hybrid-Analysis to pull up the list of contacted hosts, we find the following domains and IP addresses to verify with

None of the IP Addresses match. Hence we can assume that the C2 Server was not contacted. What are we doing wrong here?
Now, for further verification let’s use the Relations tab of VirusTotal (corresponding to the malicious file)
We finally strike gold here.
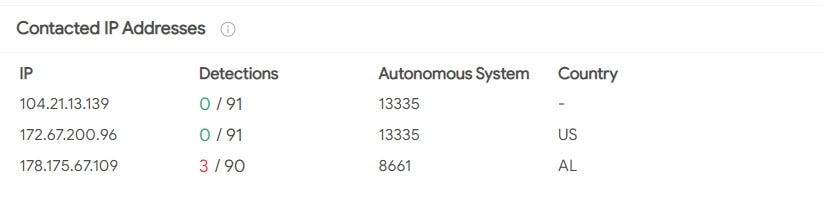
172.67.200.96 can be labeled as the IP Address of the C2 Server and it has been accessed by the NicolasPRD endpoint (victim host)
A)Accessed
Containment
Please go to the “EDR” page and contain the user machine!
Endpoint Security After containment please click “Next” buttton to finish playbook.
Proceed to contain the NicolasPRD endpoint

Add Artifacts
We have identified the domains contacted by the malicious file, as well as its MD5 hash, from VirusTotal
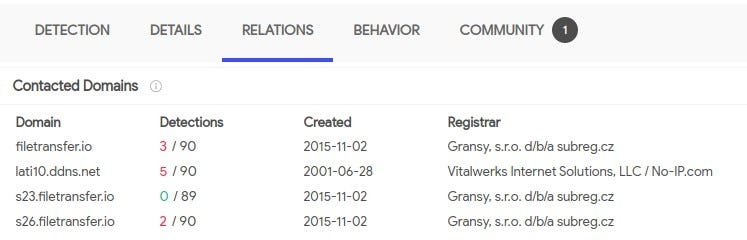
We proceed to compile this into our Artifacts chart


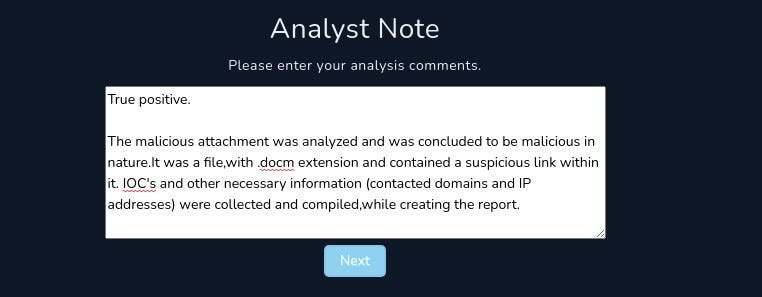
Analyst Note
Detail this section as much as you can. A good SOC Analyst gives attention to detail.
Finish the playbook Close the alert
Alert Scorecard
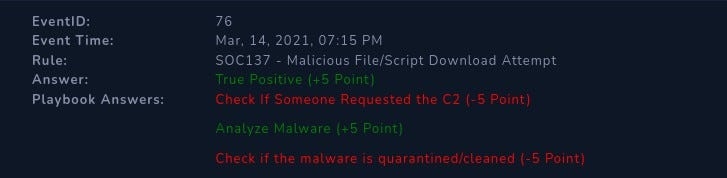
Ok, that was unexpected.
Every alert solved is a step towards perfection and I am pretty happy with the score I received.
Summary of the alert
The SOC Analyst was given a zip file, from which a .docm file containing a suspicious link was extracted. This file was subsequently detected and was found to be malicious.IOCs relating to the file, along with contacted hosts were collected, culminating in the containment of the NicolasPRD endpoint (victim host)
Conclusion
Thank you for reading this blog entry, and stay tuned as I try to close down more SOC alerts……
Your opinion matters
My audience has a voice. Feel free to reach out to me, on my socials (links are on top of this page) for any queries to be addressed. Dropping a sweet message would make my day
Let your opinion about this write-up be known, by selecting any one of the emojis below!
Last updated