SOC104 - Malware Detected Alert
Malware disguised as a WinRAR clone? Let's investigate....
Introduction to the Alert


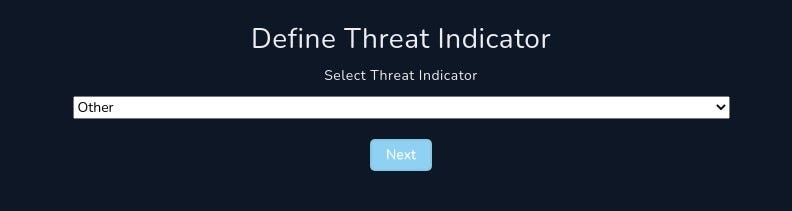
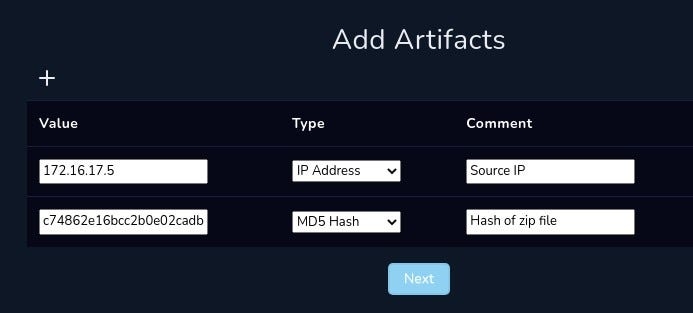
Define Threat Indicator
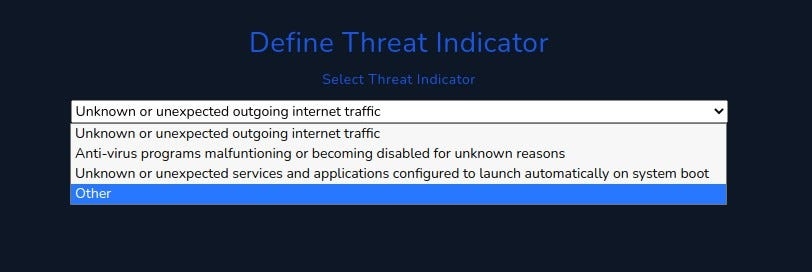
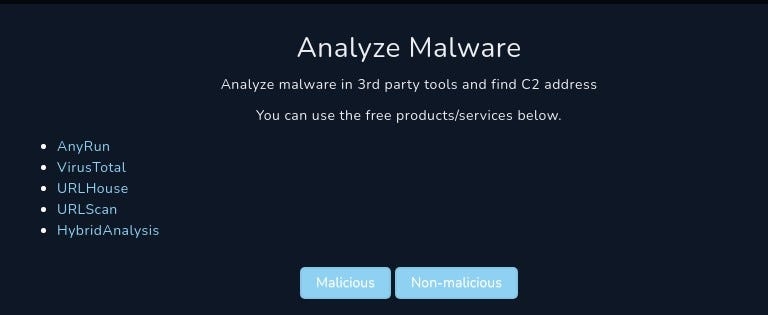
Enumeration and Analysis
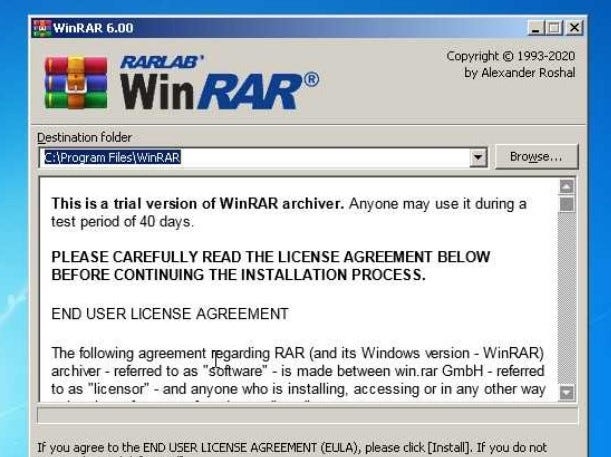
Analysis with Anyrun
Analysis with VirusTotal


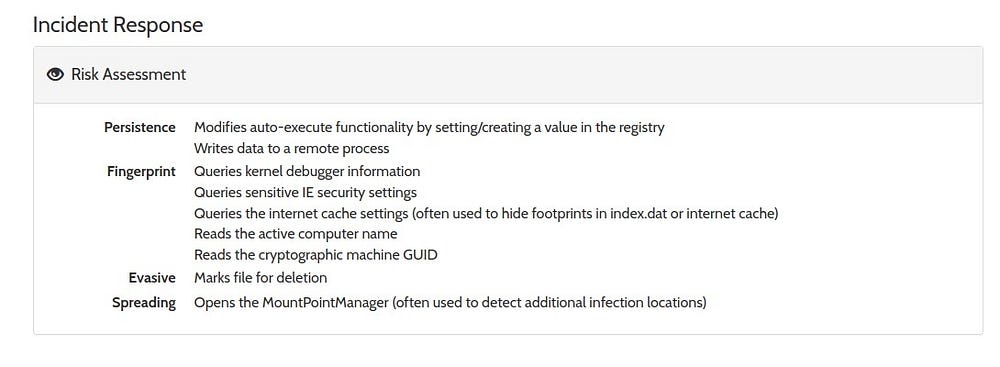
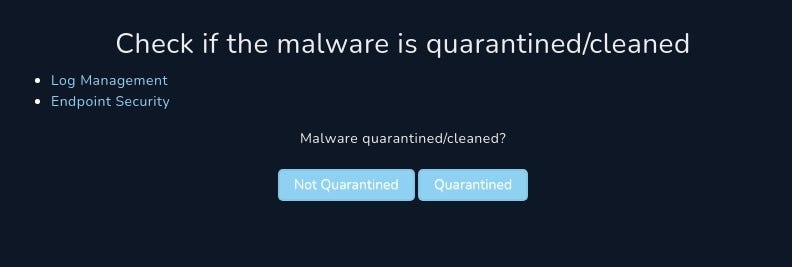
Check if the malware is quarantined/cleaned
Analyze Malware
Add Artifacts
Analyst Note

Alert Scorecard
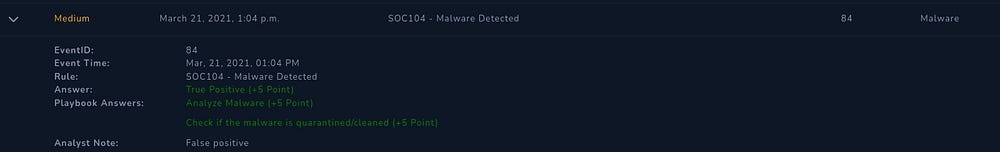
Summary of the alert
Conclusion
Your opinion matters
Last updated