SOC109 - Emotet Malware Detected Alert
Malware you say? Let's have a look at it
Hello, blue teamers and welcome to this blog entry, as I attempt to solve Let’s Defend ’s SOC109 — Emotet Malware alert. It was fun to work with real-world malware and trace back its origins and characteristics.
Keep your investigation armor at the ready!
NOTE: Always remember to investigate alerts from Let's Defend, on a VM.
Introduction to the Alert
We are met with the following alert summary, which will prove beneficial as we keep investigating
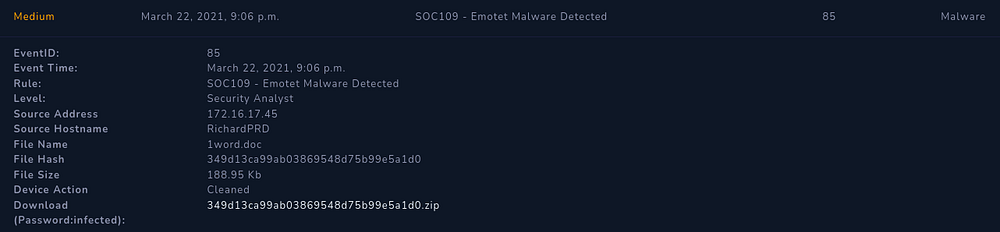
Proceed to download the 349d13ca99ab03869548d75b99e5a1d0.zip file
Next steps:-
Proceed to take ownership of the case Create case
We receive the incident details, with all necessary information for our investigation

Now, let’s start the playbook
Playbook Questions
Detection of Threat Indicator
To detect the Threat Indicator, let’s first analyze the attached zip sample
Upon unzipping it, we get a file named ‘1word.doc’
It would be wise to open it on Anyrun
Two .exe files execute as we open it (namely powershell.exe and ntvdm.exe)
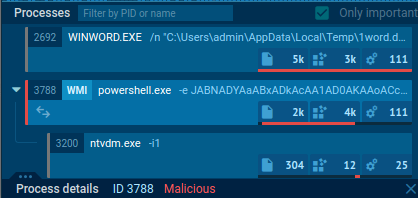
What does the PowerShell file do?
Expanding the log to find more information, we get:-

Check if the malware is quarantined/cleaned

Go to the ‘Endpoint Security section and contain the victim host(RichardPRD)

A) Quarantined
Analyzing the Malware sample
Q) Analyze malware in 3rd party tools and find C2 address
You can use the free products/services below.
AnyRun VirusTotal URLHouse URLScan HybridAnalysis
Let’s enumerate once more, using Anyrun tool

The file is malicious
A) Malicious
Check If Someone Requested the C2 Server
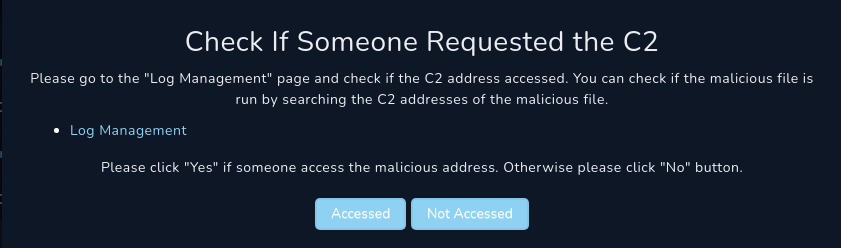
Q) Please go to the “Log Management” page and check if the C2 address accessed. You can check if the malicious file is run by searching the C2 addresses of the malicious file.
Please click “Yes” if someone access the malicious address. Otherwise please click “No” button.

Searching ‘Log Management’, for the victim host, we get 7 connection log entries

We know for a fact that Emotet spreads via phishing emails, so it is wise to limit ourselves to ports 80 and 443 connection attempts
Keeping a note of these IP’s, let’s see the related IP Addresses that have been contacted from this malicious file(can be received from the ‘Relations’ tab under VirusTotal)
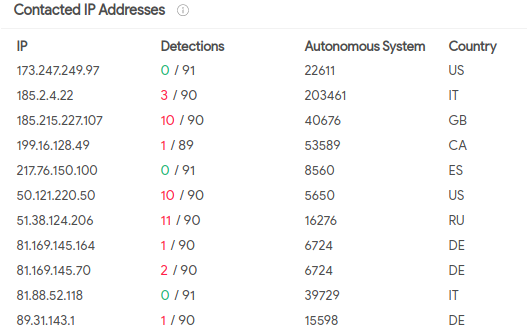
We can safely assume that the C2 Server was never accessed because none of the IP’s match with the ones found in the Log Management section
From my research, I found that Emotet uses disposable C2 servers to propagate
A) Not accessed

Adding case artifacts
From Hybrid-Analysis, let’s note down outgoing traffic from this malicious file, to be added to our collection of artifacts
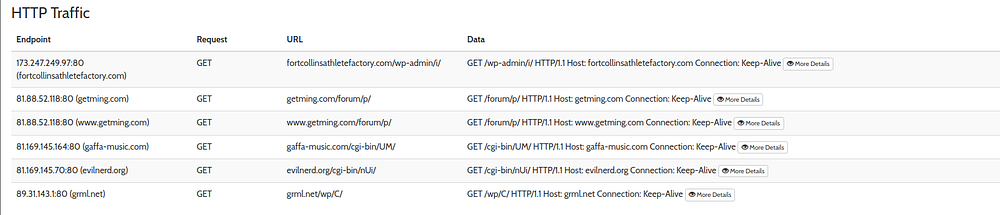
This finally boils down to:-

Analyst's Notes
We fill in the necessary details

Finish the playbook
Alert Scorecard
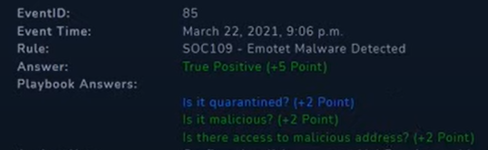
Not bad, not bad at all!
Every alert solved is a step towards perfection and I am pretty happy with the score I received.
Summary of the alert
A phishing mail was sent from the source, disguised as a harmless document, which the receiver did not fall victim to. The attachment was responsibly analyzed and determined to have connections to the Emotet malware
The case was a true positive for a phishing attack and the analyst responsibly provided artifacts and notes, discussing the case characteristics and results.
Conclusion
Thank you for reading this blog entry, and stay tuned as I try to close down more SOC alerts……
Your opinion matters
My audience has a voice. Feel free to reach out to me, on my socials (links are on top of this page) for any queries to be addressed. Dropping a sweet message would make my day
Let your opinion about this write-up be known, by selecting any one of the emojis below!
Last updated