HTTP Basic Auth: Let's Defend DFIR Challenge
Some HTTP packet sniffing.....

Hello, blue teamers! Welcome to this latest blog post, as I document my methodology of solving the HTTP Basic Auth challenge on Let’s Defend. Let’s go hunting after this .pcap file
NOTE: Always remember to investigate challenges from Let's Defend, on a VM
Gist of Challenge
We got some log indicates the attacker, can you gathering information from pcap file?
Log file: https://app.letsdefend.io/download/downloadfile/webserver.em0.zip Pass: 321
Challenge Questions
Q) How many HTTP GET requests are in pcap?
You can solve this question in two ways
Navigate to Statistics ->HTTP ->Requests,where we can find:-
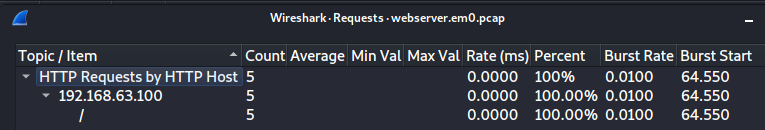
or
Enter the following query on the search tab — http.request.method==”GET”
Where we find the following GET request packets
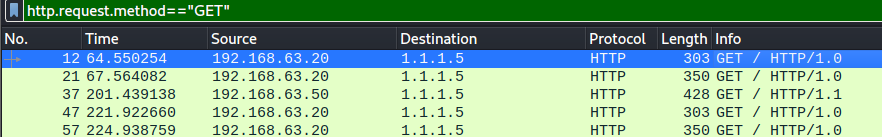
A) 5
Q) What is the server operating system?
When analyzing one of the HTTP GET request packets, from the .pcap file, we can find the following information:-
Web Server version OpenSSL Version Server Distro Name
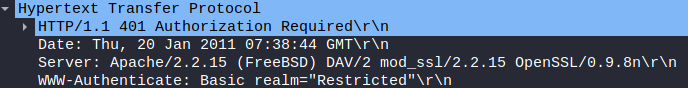
A) FreeBSD
Q) What is the name and version of the web server software?
It is visible from the User-Agent section of the packet
A) Apache/2.2.15
Q) What is the version of OpenSSL running on the server?
A) OpenSSL/0.9.8n
Q) What is the client’s user-agent information?
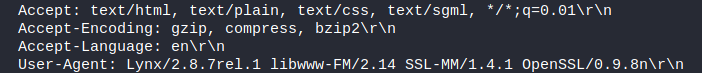
A) Lynx/2.8.7rel.1 libwww-FM/2.14 SSL-MM/1.4.1 OpenSSL/0.9.8n
Q) What is the username used for Basic Authentication?
Hunting through the GET requests, we find this username and password entered for authentication purposes
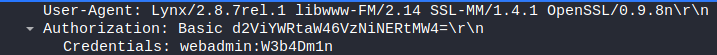
A) webadmin
Q) What is the user password used for Basic Authentication?
A) W3b4Dm1n
Conclusion
This challenge was a breeze!
Thank you for reading this entry. Stay tuned, as I go hunting behind some pcap files out there....
Your opinion matters
My audience has a voice. Feel free to reach out to me, on my socials (links are on the side of this page) for any queries to be addressed. Dropping a sweet message would make my day
Let your opinion about this write-up be known, selecting any one of the emojis below!
Last updated