SOC145 - Ransomware Detected Alert
Ransomware, you say? Let's have a look at it
Welcome to this blog entry,as I document my journey,into the world of blue teaming.We will be tackling the “SOC145 — Ransomware Detected” case on the Let’s Defend platform,which is of hard difficulty
Let’s jump head first into it.
NOTE: Always remember to investigate alerts from Let's Defend, on a VM.
Introduction to the Alert
Alert particulars provided to the analyst:-
We first take a look at the mailbox, to find any pointers about the case —which we couldn't find
Enumeration
Now take the IP Address — 172.16.17.88 and perform a check on the endpoint and log sections
We get this from the Endpoint section, giving a description about the source IP Address’ host machine
Endpoint Machine Name — MarkPRD
Windows 10 OS
User name — MarkGuna
Last Login — Aug 29 2020 08:12 PM
No entries were found for Browser, Network, or Command History. We get these entries for Process List, however:-
We get a corresponding match for someone named Mark, receiving a mail on Aug 29, when conducting a more thorough search in the LetsDefend mailbox
Analysis of Evidence
Having performed initial enumeration, let's download the file and unzip it, using the passphrase: infected
We uncover a file named ab.bin.Running file command against it tells us that it is an executable file, with GUI Interface
Next, we take the file for analysis on VirusTotal and Hybrid-Analysis tools
Reconnaissance using Hybrid-Analysis
Hybrid Analysis — (File is classified as Ransomware)
Related Hash — d5e2584ff2c17966ac150adfaeaab508af50354c7611884d64207d9c5d6b969c
File Analysis of the file on Hybrid-Analysis brings us:-
Reconnaisance using VirusTotal
VirusTotal — 60/68 vendors find the file suspicious
Threat Name — Avaddon (dark web intelligence)
MD5 Hash of malicious file — 0b486fe0503524cfe4726a4022fa6a68
Executed Shell commands and process tree of the suspected file
More notes about the ransomware file
No relevant HTTP Traffic or DNS Requests for this file(checked on Hybrid Analysis).This is a big blow, as we don't know the origin (country) of the ransomware
IOC’s of infected file—Suspicious and Malicious
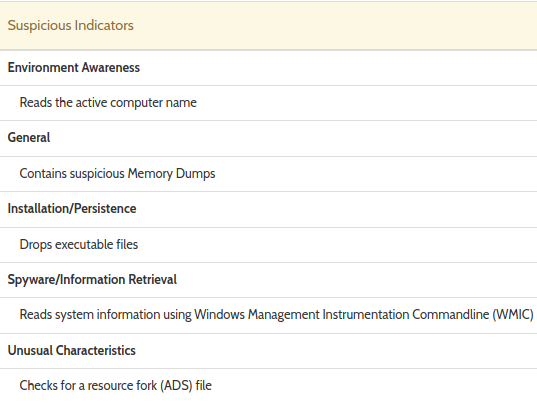

Steps to solve and close this Ransomware alert
Create a case
We select ‘Other threat indicator’ as classification for this file Malware quarratined or not? — No File is malicious or not? — Yes Check if any address accessed this malicious file? — Yes (we found IP- 81.169.145.105 had accessed this file,from the Log section)
Contain the machine — Yes
Now,we add artifacts to the case:-
IP Address 81.169.145.105 — Address that accessed the malicious file
IP Address 172.16.17.88 — Source address of ransomware
MD5 Hash 0b486fe0503524cfe4726a4022fa6a68 — Hash of file
Finish Playbook
Close the alert and state that it is a true positive
Alert Scorecard

15/20 points acquired! That’s not bad in my book!
Every alert solved is a step towards perfection and I am pretty happy with the score I received.
Summary of the alert
A SOC alert came in, detailing the case as Ransomware. Analyzing the file brought us to the conclusion that it was a binary file. Further enumeration found that the file was flagged previously on security and sandbox platforms, where we were able to gather more intelligence about the suspected file, concluding the alert to be a true positive
Conclusion
Thank you for reading this blog entry, and stay tuned as I try to close down more SOC alerts……
Your opinion matters
My audience has a voice. Feel free to reach out to me, on my socials (links are on top of this page) for any queries to be addressed. Dropping a sweet message would make my day
Let your opinion about this write-up be known, by selecting any one of the emojis below!
Last updated