WiCYS Cyberstart (Barcelona) Challenge 3
Curling your way to find some hidden content...

Briefing L03 C03
Off Balance
We’re hot on the heels of catching this cyber gang but the closer we get the more damage they try to inflict onto the Barcelona tourism industry! This time, they’ve hacked into a large international bank’s mobile application. Customers of the bank are complaining they can’t see their current balance. Intern, help customers retrieve their balances so they can continue to spend their money during their well-earned holidays!
Tip: Bypass the calculator lock to get the flag.
We can find this banking app —with sections for Recent Transactions, Payments, and Account Balances. The third section of the app is where we have a problem.
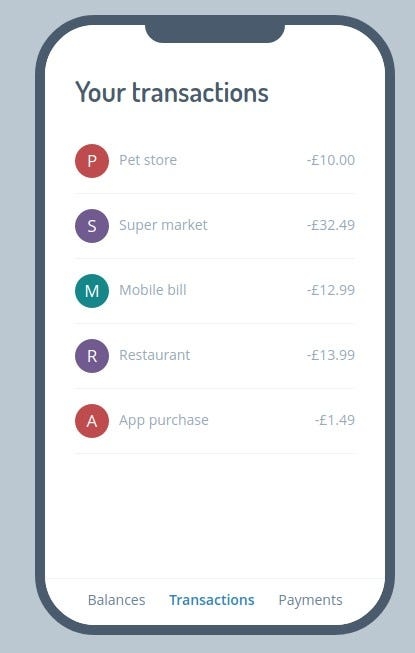
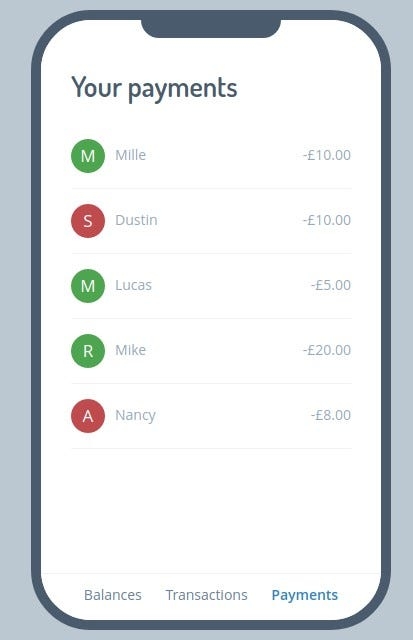
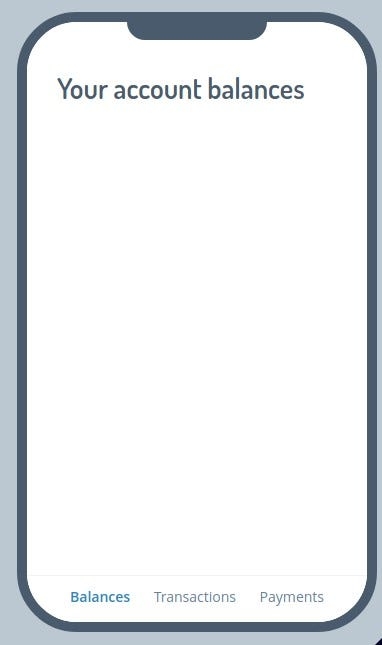
So our objective is to find the contents of the Balances page
How do we go about that?
Open the source code and head over to the 'Network' section, where we find the following web paths.
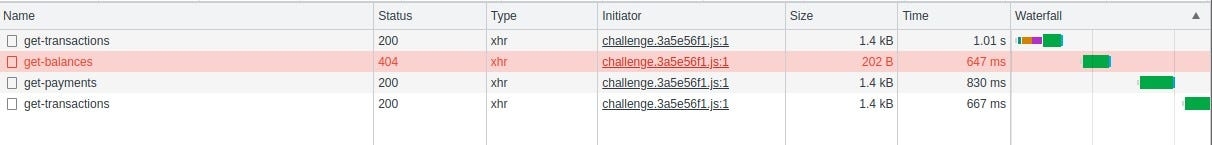
As seen in the picture /get-balances path is currently facing a 404 error and is unreachable. The rest are perfectly fine.
Extend ‘/get-balances to get more information about the path
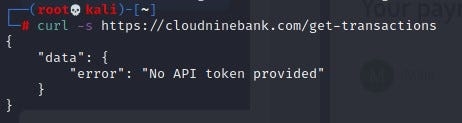
To test the connection, let's cURL the connection to /get-transactions. Use your Kali’s CLI interface for this
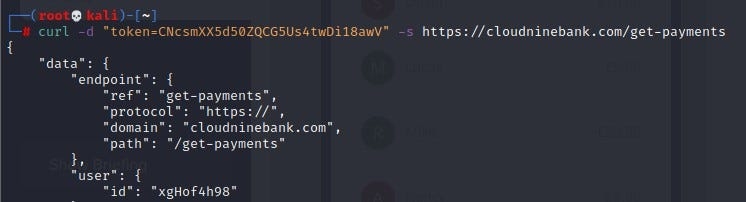
A token is required as additional data to the URL. This can be found in the Payload section of the Inspect Element. Let’s now test a working web path.I chose /get-payments
Adding it to our curl command, we get:-
Now, let's proceed to test /get-balances
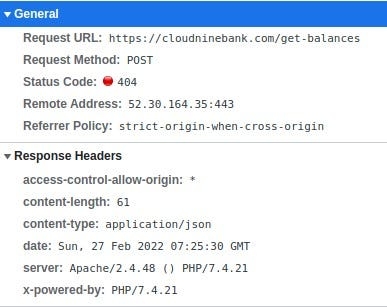
What we get is a “Resource not found” reply.
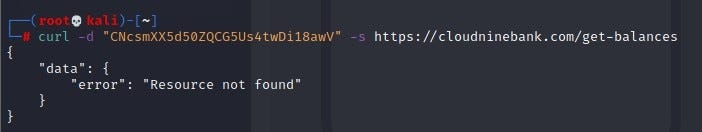
See, the stark difference
Flag Capture
Seeing no other tweaks to make, now let’s curl the main website
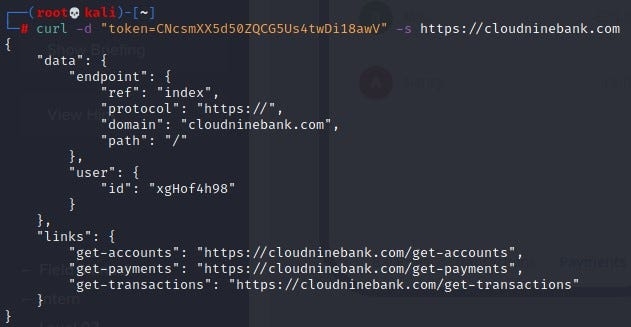
Hey, hey what do we notice here? Instead of get-balances entry, we find a path get-accounts. Let’s curl that instead, using the token value
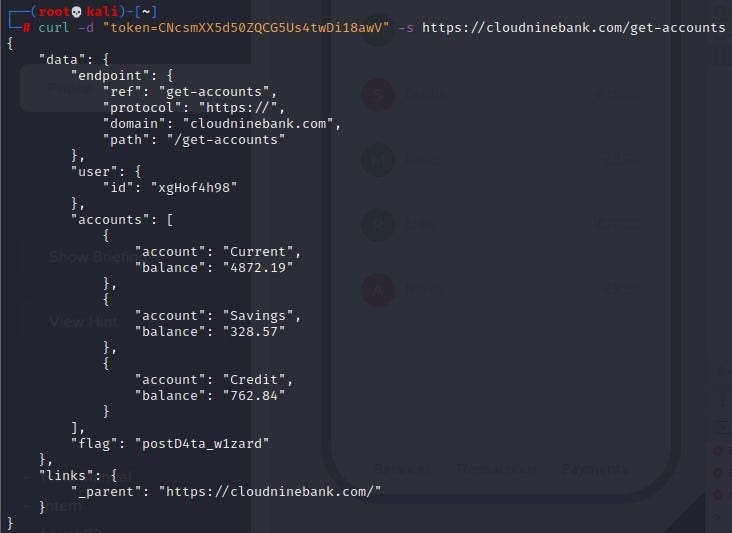
As you notice, the flag is present towards the bottom
Flag — postD4ta_w1zard
Submit it and onward ahoy to the next challenge.
Scoreboard

Last updated