WiCYS CyberStart (Barcelona) Challenge 4

Briefing L03 C04
The Final Countdown

The main tourism website for Barcelona has been hacked. They’ve devised a program that changes the content of the website based on a timer. You can imagine the confusion this has been causing the sites visitors! Can you figure out how we can get the secret code to stop this program from running?
Tip: The characters at the 5 URLs change quickly, but computers can be far quicker than humans, especially when getting data!
Proceeding to the challenge, we are given a set of links
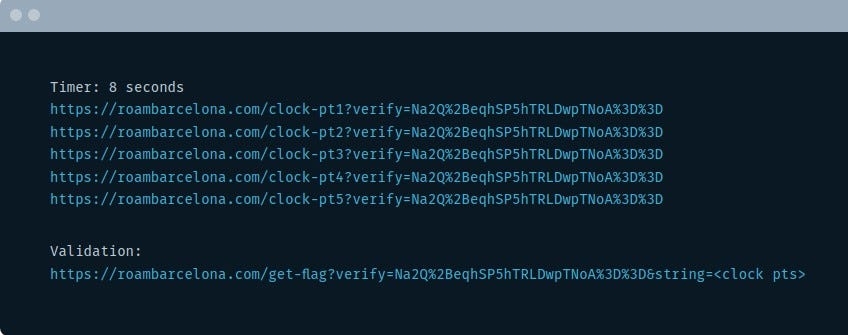
So what's the objective?
Clicking on each of the 5 links (under the timing section) gives us 5 different strings, which together form a passphrase.
The challenge here is that the strings need to be collected in under 10 seconds and inserted as parameters in the validation link
How do we collect the strings effectively?
cURL to the rescue again!
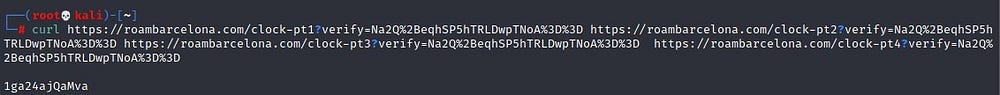
Step 1 - curl all the links to get the strings we want (do not list each of them in separate lines!)
Why? — we are aiming to collect data from the websites. In this case, we are using curl to aid us.
It should look something like this. Keep this ready, before the timer is up
Step 2 - Take the validation link and open it in another browser. Clear the string parameter and leave it empty
Execution Time!
Run the curl command (when timer resets to 10) and quickly insert the generated passphrase from the CLI to the end of the validation string
Voila, you get your flag!

Flag — wh1te_Ro$E
Scoreboard


Well fellow gamers, my internship time is up, as I am on a free CyberStart license (up to 3 levels only). I had a great time completing challenges (both easy and challenging) and drafting writeups for the same. Hope you enjoyed the time spent on CyberStart.
Until then, farewell. Stay connected on my socials (given at the top of this page). Dropping a sweet message would make my day
Last updated